
Who is really responsible for cloud security?
At a recent NetEvents EMEA Press Spotlight the question was raised about security in the cloud, and where the final responsibility for it lies.
Ovum analyst Rik Turner was surprised by the number of people who were not aware of the "Shared Responsibility Model" summarising three different ways of consuming cloud services – Infrastructure as a Service (IaaS), Platform as a Service (PaaS) and Software as a Service (SaaS) – and the relative responsibilities of the customer and the cloud supplier illustrated in the diagram below.
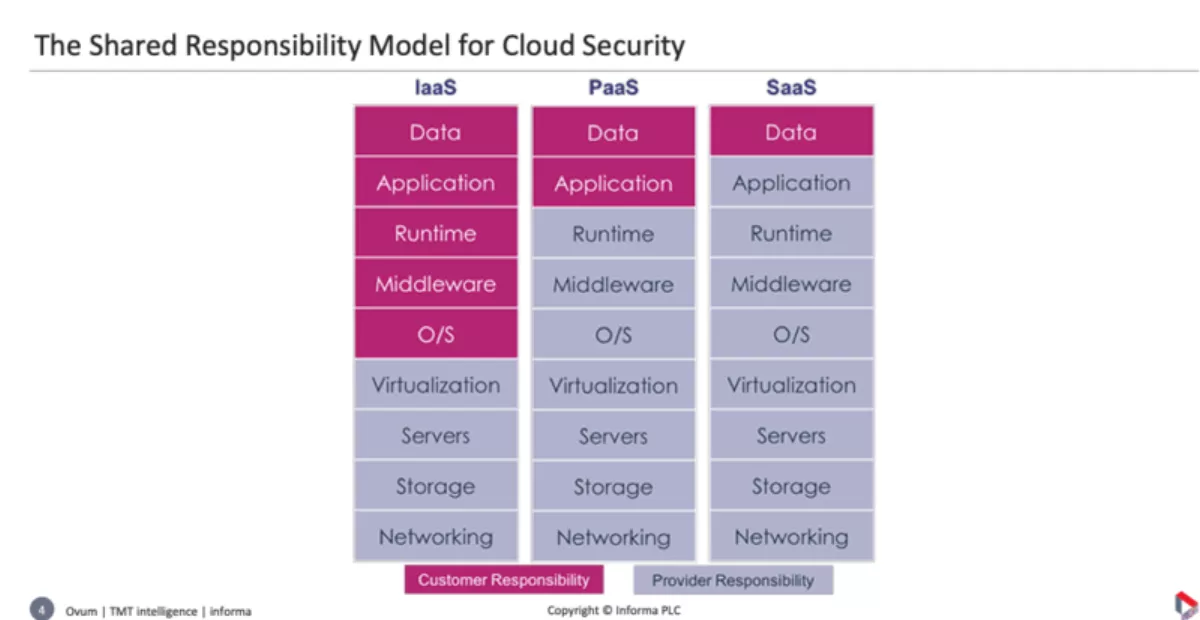
In IaaS for example: Amazon Web Services (AWS) take care of all the grey sections, from Virtualization down to Networking, but above that it's the customers' responsibility.
"You are not going to get any money back from them if you are breached because you didn't secure those layers above," says Turner.
Similarly, for PaaS, you are responsible for security in the top two layers.
"If anything goes wrong with any of that, AWS would have to refund some money.
The shared security model is important for any enterprise migrating to the cloud: the enterprise will have to take care of security in all the red sections.
These are the parts security vendors build their enterprise services on.
The joy and the temptation of SaaS is that it is so easy to buy without IT even needing to be involved.
Hence the threat of shadow IT, and the rise of Cloud Access Security Brokers (CASB) as the initial response.
Since then, the CASBs have mostly been acquired by larger security companies with broader portfolios.
IaaS and PaaS are more complicated for the enterprise because the customer has a broader responsibility and there is more use of containers, microservices, or serverless services - each with their own format.
It's a progression: VMs remove the dependence on physical servers; containers spare the spinning up of new VMs, and serverless means you can forget these and just specify the functions to be supported – with a 70-80% saving in infrastructure costs.
As a consequence, we are hearing more about Cloud Workload Protection Platforms – blocking and remediating attacks, and restarting the workload somewhere else – and Cloud Security Posture Management (CSPM), which is essentially a compliance function.
It's so easy now to spin up a Virtual Machine (VM) so CSPM monitors and manages the spread of VMs to ensure compliance with company policies.
According to Turner, these two worlds should ultimately converge, because CSPM is starting to move in the direction of remediation, rather than simply alerting.
"It gets a little bit more difficult with containers, in as much as you are starting to see smaller packages of code. Things become more ephemeral with serverless.
"The life of a piece of code that's running in a serverless environment may be a matter of milliseconds. How do I secure that?
His suggestion is that we are moving towards a DevSecOps world, where the developers become responsible for embedding the security.
Some people who struggle with security use the cloud as a fallback.
That was the opinion of BA Test Labs director Jan Guldentops.
"We're going to outsource to the cloud as it's all secure and all the problems are gone. That's the first misconception I see all the time. We are going to the cloud just to be able to secure.
Is that really so? Others, like nCipher Security chief strategy and marketing officer Peter Galvin, disagree and say the main cloud driver is not security, but agility and reducing spending on data centers.
The real problem is companies migrating ASAP to a fast-evolving cloud without upgrading their thinking: what used to be best practice is now actually wrong.

