Locky ransomware's 'rebirth' puts everyone at risk once again
The Locky ransomware is back and using social engineering in another round of email-based attacks on tens of thousands of users, according to a new report from Comodo's Threat Intelligence Lab.
The company is calling the resurgence of Locky a 'rebirth', noting that the new ransomware campaign began on August 9 and is continuing to appear in inboxes.
The attack is housed in email with an attachment and either little or no content in the body. The attachment name varies, however the basic format is the same: "E 2017-08-09 (580)". While the extension and filenames '(580)' change frequently, the email always contains an unknown file.

According to researchers, the attachment downloads IKARUSdilapidated, which is the newest variant of Locky.
Because it is a new variant, most organisations' security programs read it as an 'unknown file'. For those who do not use a 'default deny' security posture, they could easily be infected by the ransomware, Comodo claims.
'Default deny' security postures work by denying all unknown files until they are verified as 'good' files.
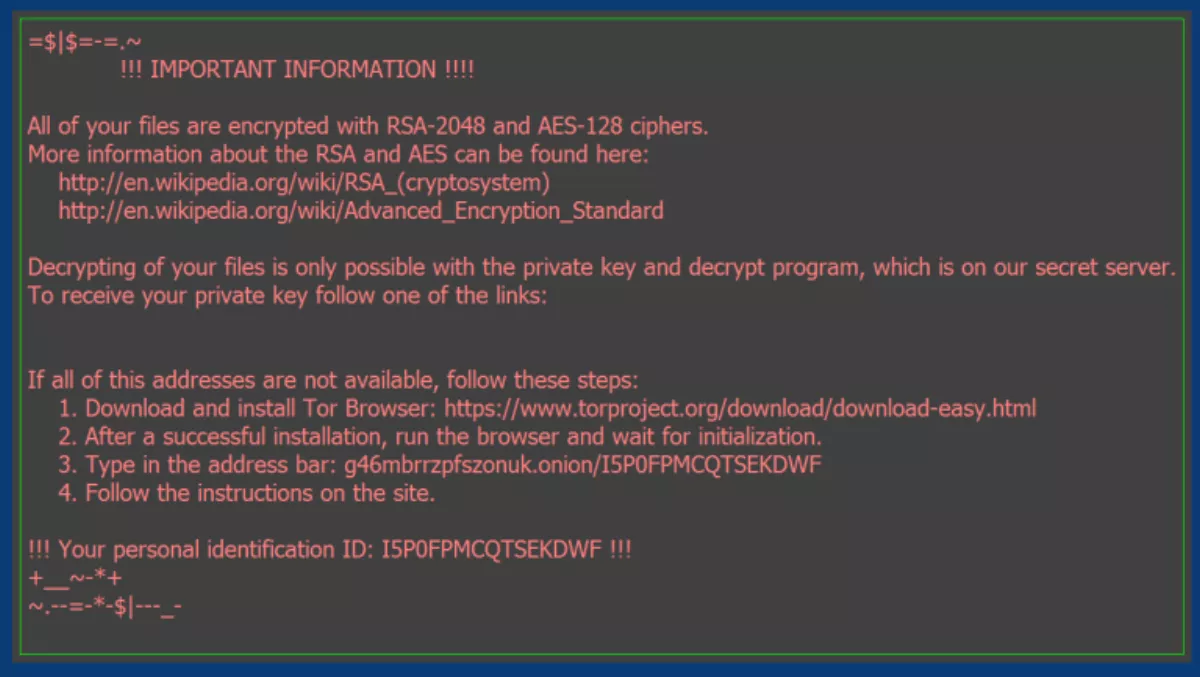
When users click on the attachment, macros save and run a file that contains the Trojan. That Trojan then encrypts all files that match certain extensions. Users are then asked to download anonymous browsing platform Tor, which is used to facilitate the ransom demand.
The ransom amount varies between 0.5-1 bitcoin, which is equal to NZD$2773-$5546.

While most targets have been in Indonesia, India, Vietnam, India and Mexico, the phishing campaign is targeting 11,625 across 133 different countries.
Most victims have been telecommunications firms and Internet Service Providers. Researchers suggest these industries have been targeted to set up a botnet with a complex command and control architecture.
Comodo Threat Intelligence Lab head Fatih Orhan says that the attack was an interesting case in terms of its sophistication and scale of attack through the botnet.
"When artificial intelligence couldn't identify these unknown files, the full resources of the lab were needed to analyze and identify the code in the file and render a verdict; in this case the verdict was "bad" and we've now added it to our blacklist and malware signature list," he says.
The Locky ransomware has been through many iterations since its 2016 discovery. It generally used the same tactic of an email with an attachment that runs the code and launches the ransomware.
According to Malwarebytes researchers, the Locky malware is difficult to predict.
"Over the last few months, Locky has drastically decreased its distribution, even failed to be distributed at all, then popped back up again, vanished and reappeared once more," Malwarebytes researchers state in a blog.
The ups and downs of Locky remain shrouded in mystery. One thing time has taught us is that we should never assume Locky is gone simply because it's not active at a particular given time," they conclude.


